Analyze POST and GET packets using WireShark

Wireshark is used to analyze inbound and outbound packets from your system. I don’t know how others use it but I use to monitor the GET and POST requests that are being sent from my machine. This helps me analyze the exact data that is being sent to a particular website. You can download wireshark for free, so I would recommend everyone to install it. It is not only informative and helps in troubleshooting but it is fun to watch what is going on behind the scenes.
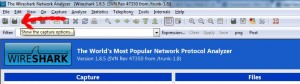
Once you have installed Wireshark, run the application. Click on “Show capture options”. Refer the screenshot below if you are unable to locate the button.
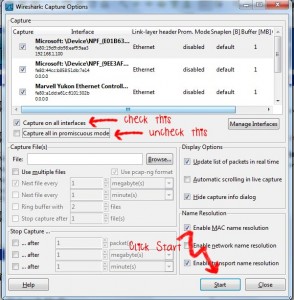
You will now need to configure the capture options. Follow these steps :
- Check Capture on all interfaces
- Uncheck Capture all in promiscuous mode
- Click Start
Immediately the packets start getting captured and you can view them in the Wireshark window. Observe the protocol of the packets, it tells us what protocol is being used to transfer the packet. This helps us filter out only those packets that we need and leave the rest. Now as we need to find the GET and POST packets (which follow the HTTP protocol) we need to set an appropriate filter for it.
Notice the filter text box. Paste the following expression in it, http.request.method == GET or http.request.method == POST and hit enter. You can save it for future use as well, so that you don’t need to remember it everytime you wish to filter packets.
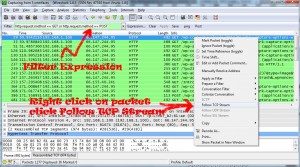
Here’s how the final result looks like :
Right click on the packet which you wish to analyze and click on “Follow TCP Stream”. A new window will open with all the details of data sent and received. To be more accurate, the “request” sent and the “response” received. Here’s how to read the details from the new window.
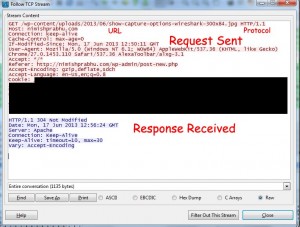
I will just try to explain the packet that I chose to analyze in this example. The one you choose might be completely different but the basics remain the same. Observe the following details in the text that is visible.
- GET indicates the method used (GET or POST)
- URL indicates the URL to which the request is being sent.
- The protocol in this case will obviously be HTTP. It also shows the version, i.e. 1.1
- If-Modified-Since is one of the header messages, it indicates that the request is just to check if the URL is modified since the time specified. (As you can see, in Response message, all we get back is “Not Modified”)
- User-Agent contains information about the browser used.
- Referer indicates the URL from which the request was referred.
- Accept-Encoding is also one of the header message which indicates the different encoding methods that can be decoded by the browser from which the request is being sent.
- Cookie, contains the data that is being stored in cookies of your current browser.
We can read the response in a similar manner :
- HTTP/1.1 indicates the protocol/version used.
- 304 is the status code for “Not Modified”. You can find all HTTP status codes on w3.org page.
- Date indicates the time during which the response was generated.
So now that you know how to analyze packets using Wireshark, go try your hands at it and see what data is being sent to which sites. You will be surprised to know how many chrome extensions sent data to their servers behind your back. Check out the various packets the torrent client keeps sending and receiving. Internet won’t be the same for you anymore.


Good Article, Thanks
Hi, I tried to get POST info by adding filter (http.request.method == GET or http.request.method == POST ) but I am seen only GET request ??
KC
helpful… thanks